RESOURCES Security Awareness
The best ways to build cyber security resilience in your organisation is to have strong systems in place and staff that are well-informed of security risks and follow best-practices.
Check out below guidance and video trainings to help you detect and respond to phishing attacks and other cybersecurity threats.
Phishing Attacks
If you think you’ve been sent a phishing email, here’s what to do next.
- If you haven’t done anything with the email, delete it.
- If you gave out some personal or financial details:
- contact us and tell us what happened
- change the passwords for any online accounts you think might be at risk
- enable Multi-Factor Authentication for any online accounts if available
- Review CERT NZ recommendations, keep calm and read on…
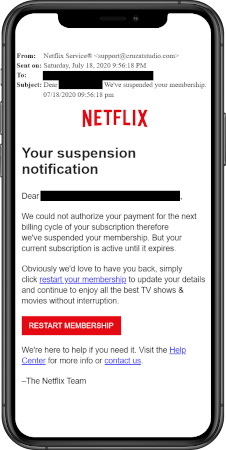
How to recognise phishing attempts
Although you can’t prevent a phishing attack, there are things you can do to make sure you recognise one:
- Know what to look for in a phishing email. You might notice that:
- you don’t recognise the sender
- the sender name doesn’t sound quite right
- you don’t recognise the name of the company
- the company logo doesn’t look like it should
- the email refers to you in a generic or odd way — for example, ‘Dear You…’
- the email contains bad grammar or spelling
- if you hover over a link in the email with your mouse, the address that you see doesn’t match the place it’s saying it’ll take you.
- Don’t click on web links sent by someone you don’t know, or that seem out of character for someone you do know. If you’re not sure about something, contact the person you think might have sent it to check first.
- Use bookmarks or favourites to access websites rather than links in emails.
- Check to see how the companies you deal with — like your bank — will contact you, so you’re more likely to recognise what’s a legitimate request and what isn’t.
- If you have your own business, make sure you keep your support contracts (with your antivirus provider or your firewall provider, for example) up to date.
- Follow us on Twitter and LinkedIn and look out for our real-life phishing examples in our Phish of the Day series.
Remember — if you don’t click on any links or attachments in a phishing email, your system is safe.
Password Training
Best practices for better passwords
Vulnerability Assessment and Penetration Testing PenTest.NZ
PenTest.NZ was provides businesses and organizations access to a suite of cyber security testing and assurance services, with cost-effectiveness being top of mind. To give you the best value, we use a commonsense approach by prioritizing critical vulnerabilities and risks, helping you to address them in the most effective way.
PenTest services can include a full Network Penetration Testing, detailed Vulnerability Assessments, Web Application Black or Gray-box PenTesting, Host and Source Code Security Review and much, much more.
All ethical hacking is done manually by certified experienced testers. Our team will identify specific risks to your business systems and data and provide proven mitigation strategies.
Pentest.nz was created to provide affordable penetration testing services for industry partners and businesses.
Private DNS Firewall Protection CyberShield
CyberShield is a managed security service utilizing a private DNS Firewall to protect all users and devices against online threats such as Phishing, Malware, Botnets, and Ransomware, leveraging global and local threat feeds at the DNS layer.
When you use CyberShield, websites that contain malware or phishing are blocked at the DNS layer. This means that no connection to the bad websites or web applications is established and users can stay safe from online threats.
CyberShield.nz provides cyber immunity using a community feedback loop threat strategy and continuous improvement to detect and respond to zero-day threats and minimize false positives.
Cyber Risk Assessment and Training CyberScient
Get CyberSmart with CyberScient is our most recent initiative and focuses on increasing cybersecurity awareness using self-assessment, training and testing.
CyberScient.com online platform provides a free Kickstarter program to help organizations and individuals learn how to protect against online threats and cyber risks.
It all started with a desire to help all businesses lift their cyber posture since SMEs are at risk more than ever before and doing nothing is no longer an option. As specialists and community members, we want to provide our customers and community cost-effective solutions to mitigate cyber security risks.
Cyber Risk Drawing Contest Platform for Kids CyberScient KIDS
CyberScient Kids platform is our pilot program to raise awareness around cyber security threats for kids and teenagers.
The CyberScient Kids acts as an awareness and drawing contest platform. In the CSKids platform, 4 to 17 years’ old can creatively express cybersecurity safety tips and catch-phrases in drawings as they see fit.
CyberScient Kids platform’s mission is to train younger generations to discover, learn, understand and adapt to all online threats they face when they go online.




